FuzzPlanner: Visually Assisting the Design of Firmware Fuzzing Campaigns
Emilio Coppa, Alessio Izzillo, Riccardo Lazzeretti, Simone Lenti
Room: 101-102
2023-10-22T03:00:00ZGMT-0600Change your timezone on the schedule page
2023-10-22T03:00:00Z
Abstract
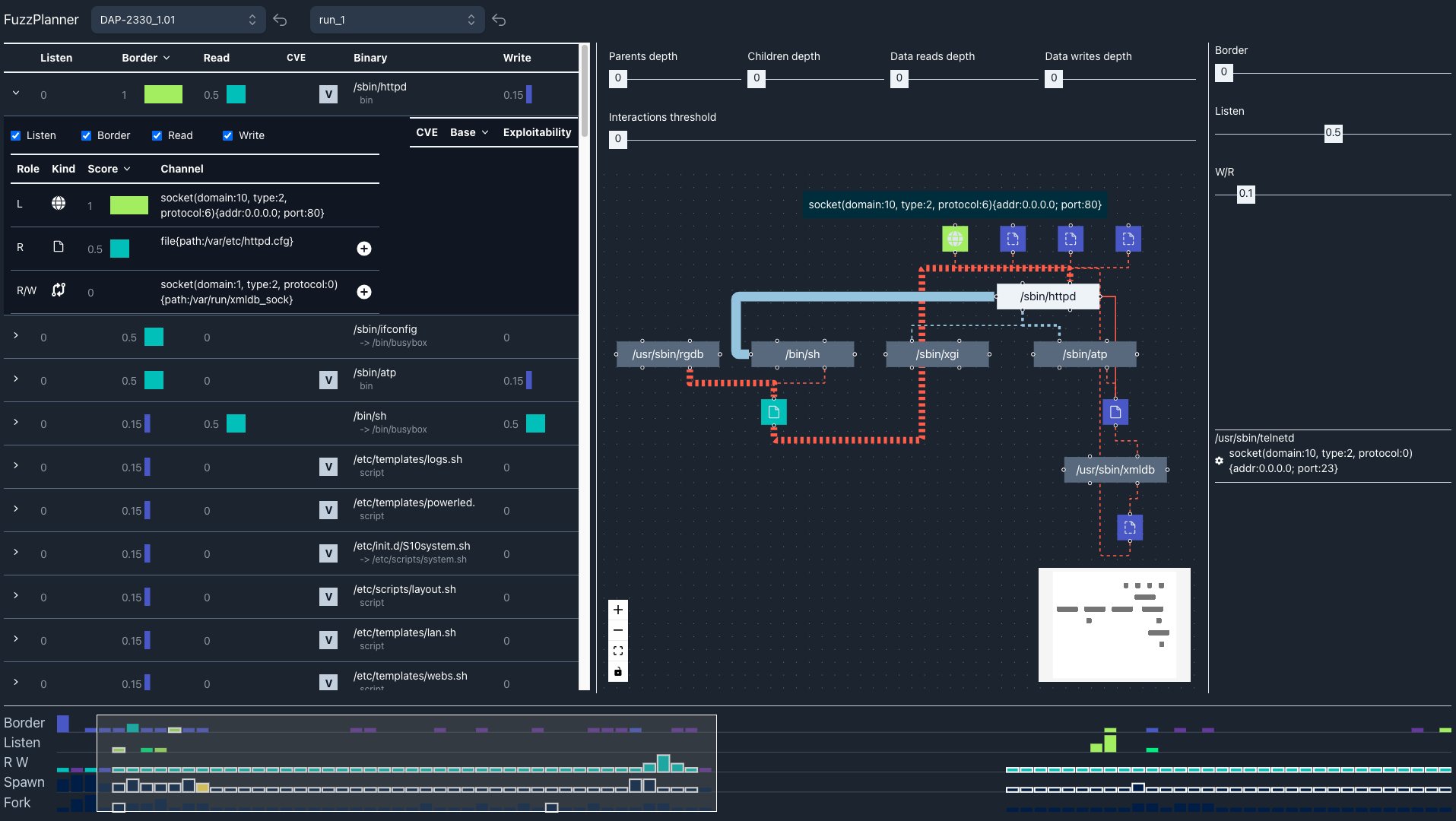
Embedded devices are pivotal in many aspects to our everyday life, acting as key elements within our critical infrastructures, e-health sector, and the IoT ecosystem. These devices ship with custom software, dubbed firmware, whose development may not have followed strict security-by-design guidelines and for which no detailed documentation may be available. Given their critical role, testing their software before deploying them is crucial. Software fuzzing is a popular software testing technique that has shown to be quite effective in the last decade. However, the firmware may contain thousands of subcomponents with unexpected interplays. Moreover, operators may have a tight time budget to perform a security evaluation, requiring focused fuzzing on the most critical subcomponents. Also, considering the lack of accurate documentation for a device, it is quite hard for a security operator to understand what to fuzz and how to fuzz a specific device firmware. In this paper, we present FuzzPlanner, a visual analytics solution that enables security operators during the design of a fuzzing campaign over a device firmware. FuzzPlanner helps the operator identify the best candidates for fuzzing using several innovative visual aids. Our contributions include introducing FuzzPlanner, exploring diverse analytical tools to pinpoint critical binaries, and showing its efficacy with two real-world firmware image scenarios.