Visual Firewall Log Analysis - At the Border Between Analytical and Appealing #9019
Marija Schufrin, Hendrik Lücke-Tieke, Jörn Kohlhammer
View presentation:2022-10-19T16:45:00ZGMT-0600Change your timezone on the schedule page
2022-10-19T16:45:00Z
The live footage of the talk, including the Q&A, can be viewed on the session page, VizSec: Best Paper Announcement and Papers.
Keywords
Human-centered computing, Visualization Techniques, Tree and Network Visualization
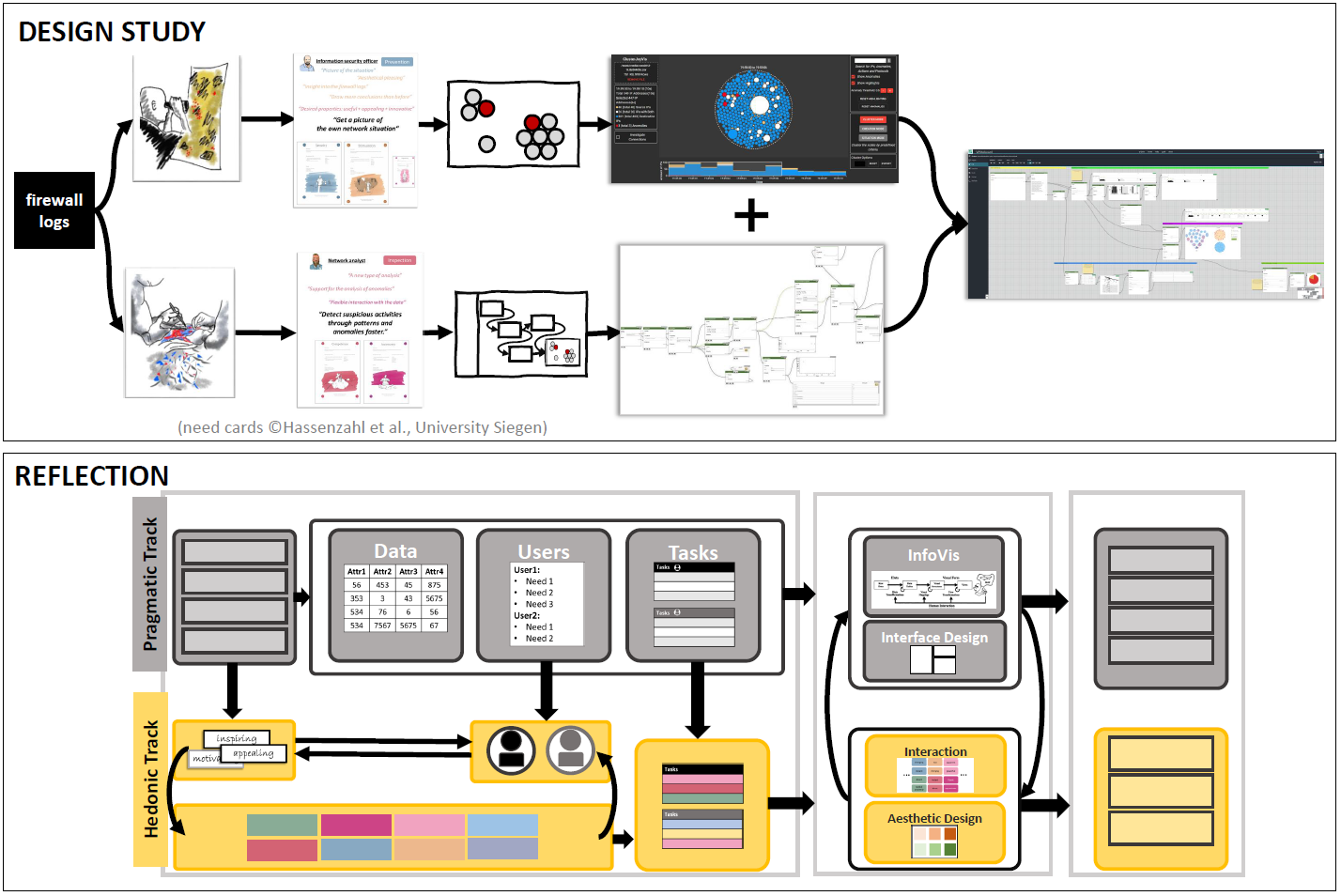
Abstract
Network security is critical for organizations to secure their network resources from intrusion and attacks. A security policy is a rule enforced in the network to allow or block network traffic. To write security policies, network analysts divide their networks into segments or parts with similar security needs. Segmentation makes writing security policies manageable and identifies more robust security policies for the network. Visualizations can help analysts to understand the segmented network and define security policies. We contribute Portola, a hybrid tree and network visualization technique to display a segmented computer network. Portola presents an overview of the segmentation as a hierarchy and displays connections within the network. Using Portola, analysts can explore a segmented network, identify nodes and connections of interest through exploratory network analysis, and drill down on elements of interest to reason about the patterns of relationships in the network. Through this work, we also discuss the goals of network analysts who work with segmented networks and discuss the lessons learned from the user-centered iterative design of Portola.